Windows’ BITS service is a middleman for your download jobs. You start a BITS job, and from that point on, BITS is responsible for the download. But what if we tell you that BITS is a careless …
Deep Web – Best Onion Links
Introduction Points Ahmia.fi – Clearnet search engine for Tor Hidden Services EasyONIONs – EasyONIONS is the easiest way to access a hidden service The Tor Dark Wiki – Latest links from Tor …
PytheM – Python Pentesting Framework
pythem is a multi-purpose pentest framework written in Python. It has been developed to be used by security researchers and security professionals. The tool intended to be used only for acts within …
Continue Reading about PytheM – Python Pentesting Framework →
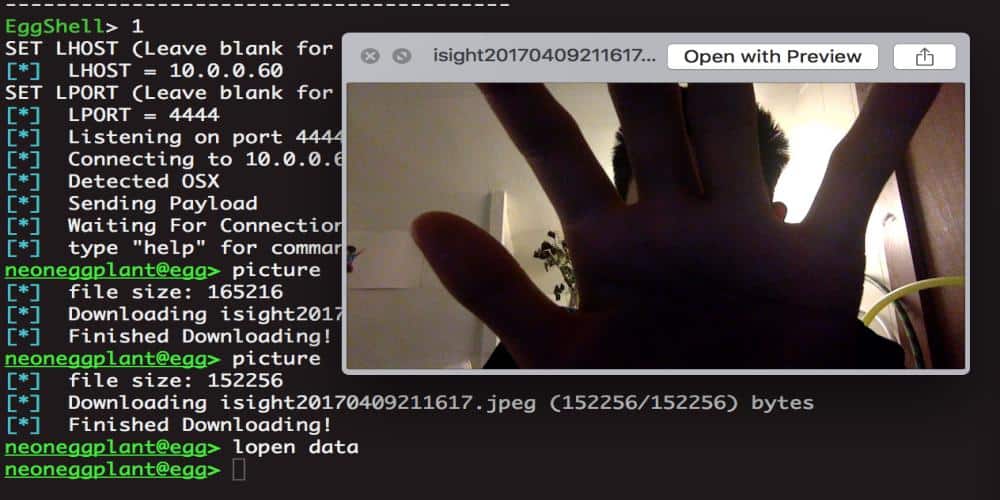
EggShell – iOS macOS Remote Administration Tool
EggShell is an iOS and macOS post exploitation surveillance pentest tool written in Python. This tool creates 1 line multi stage payloads that give you a command line session with extra functionality. …
Continue Reading about EggShell – iOS macOS Remote Administration Tool →
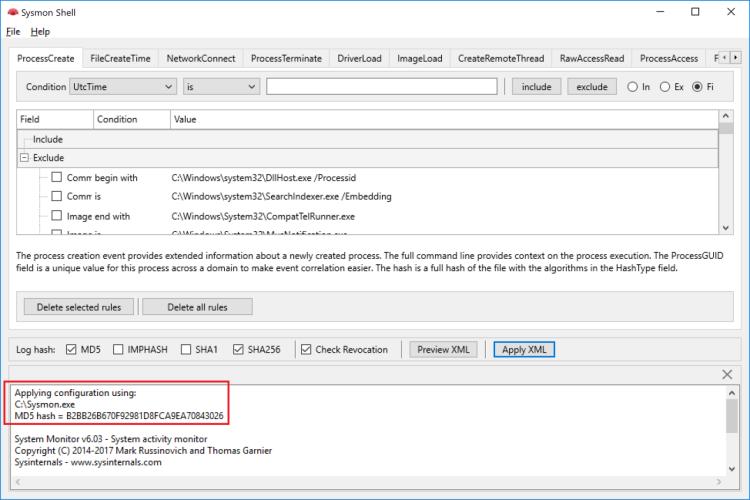
Sysmon View: Tracking and Visualizing Sysmon Logs
Sysmon Shell can aid in writing and applying Sysmon XML configuration through a simple GUI interface, it can also be used to learn more about Sysmon configuration options available with each release, …
Continue Reading about Sysmon View: Tracking and Visualizing Sysmon Logs →
Onion Decoy Server
A platform to run private unannounced Honeypots as Tor Hidden Services (aka Onion Decoys) inside the Tor Network. The Onion Decoys are implemented with Docker containers as honeypots. The reason to …