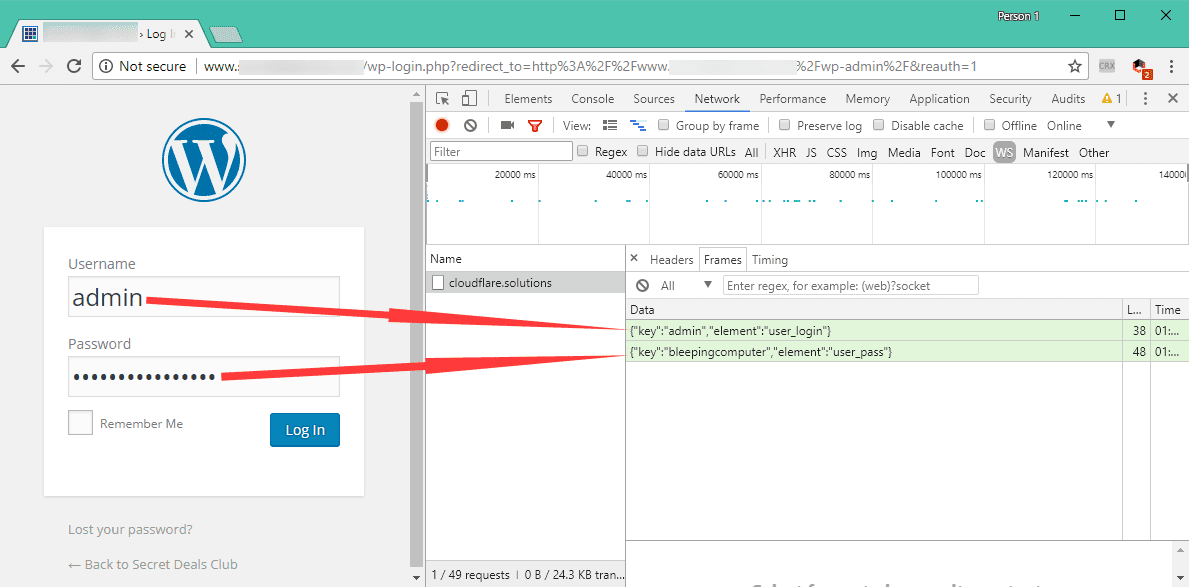
It is being loaded from “cloudflare.solutions” which is not even affiliated with CloudFlare, in any way. It logs everything which a user is typing inside form fields, as soon as the user switches away from the input field.
It is dangerous because it can log usernames and passwords while a user is in the site’s admin panel and it’s loaded on both: frontend and backend.
Another reason why this script is dangerous when left to run in the frontend… on most WP sites it can steal user data from the comment fields, but as you know WordPress can be used as an eCommerce platform. In this case, the attacker/s can steal credit card data and personal user info.
The malicious code is hidden in the functions.php file, as hackers compromised WordPress sites, via various means. This file is a standard file found in all WordPress themes.
Active since April
Sucuri has tracked at least 3 different malicious scripts hosted on the cloudflare.solutions domain. And this type of attacks aren’t that new.
The first attack took place in April, when attackers used a malicious JavaScript file, just to embed banner ads on various hacked websites.
In November, the hacker group changed it’s tactics with a fake jQuery and Google Analytics JavaScript file, which were a copy of CoinHive in-browser crypto miner. 1,833 websites were infected by the end of November.
The latest series of attack, the hackers kept the cryptojack script active, and added the Keylogger component.
Malicious script active on nearly 5,500 WordPress websites
According to PublicWWW, the malicious script is active on 5,496 sites.
From Sucuri:
As we already mentioned, the malicious code resides in the function.php file of the WordPress theme. You should remove the add_js_scripts function and all the add_action clauses that mention add_js_scripts. Given the keylogger functionality of this malware, you should consider all WordPress passwords compromised so the next mandatory step of the cleanup is changing the passwords (actually it is highly recommended after any site hack). Don’t forget to check your site for other infections too.
Leave a Reply