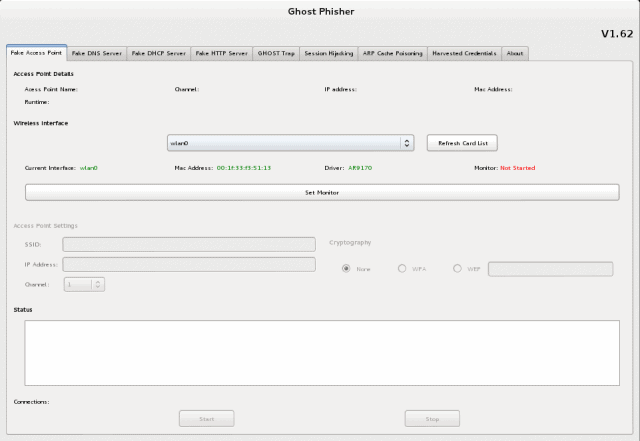
Ghost Phisher is a Wireless and Ethernet security auditing and phishing attack tool written using the Python Programming Language and the Python Qt GUI library, the program is able to emulate access …
Continue Reading about Ghost Phisher – Phishing Attack Tool with GUI →